1 Introduction / Executive Summary
Zero Trust has seen a steep increase in popularity over the past few years. While the idea and value of Zero Trust are widely accepted, most organizations still struggle to implement a Zero Trust model across cybersecurity and IAM (Identity and Access Management). The main reasons for that are the inherent complexity of a model that affects all areas of cybersecurity and the gap between an abstract concept of “don’t trust, always verify” and the practical implementation.
The gap between an abstract paradigm and concrete implementation is huge for Zero Trust. Putting Zero Trust in practice requires the right type of services and support.
Zero Trust affects various domains that are commonly split across multiple departments and sometimes even under split leadership. Ownership for Zero Trust must be unified and integration and collaboration between the various parties must be fostered.
Implementations best start at the beginning of the user journey: Authentication. This is the first verification event, followed by device verification and security, network security, and authorization. With the ubiquitous relevance of IAM for authentication and authorization, but also the management of identities, device bindings to users, and management of access entitlements, IAM takes a central role within Zero Trust.
With the inherent complexity of Zero Trust, organizations are well-advised to build on partners that bring experience, proven methods, and the ability to support along the entire Zero Trust journey, from concepts to implementation and operations.
Providers that offer the full range of services from consulting to managed services for support and operations, continuous improvements and evolution of the infrastructure are an interesting option for making Zero Trust initiatives succeed, helping in tackling the complexity with standardized methodology and services. This applies to all sizes of organizations, given that neither skills nor capacity commonly are available at the extent a journey such as the one towards Zero Trust in practice require.
1.1 Highlights
Zero Trust requires defined leadership and an integrated organization where various groups work jointly and collaboratively on a common goal.
IAM is the logical starting point for the Zero Trust journey, with authentication being the first verification of users.
The complexity of Zero Trust mandates that standardized and proven methods and concepts are utilized, building on experience, and leveraging the benefits of the economies of scale. Managed services are a logical choice.
iC Consult can build on their rich experience in delivering IAM managed services to also support organizations on their Zero Trust journey.
Leadership and organization for Zero Trust implementation
Success in Zero Trust requires strong leadership. CISOs most commonly are the ones in charge of the Zero Trust program. They must unite their teams for a joint initiative.
While Zero Trust is not a new topic in IT, it has been facing a massive increase in attention over the past three years. With the pandemic and the rapid adoption of WfA (Work from Anywhere), the pressure on IT to adapt Zero Trust concepts increased massively. However, many organizations are still stuck in the conceptual stage.
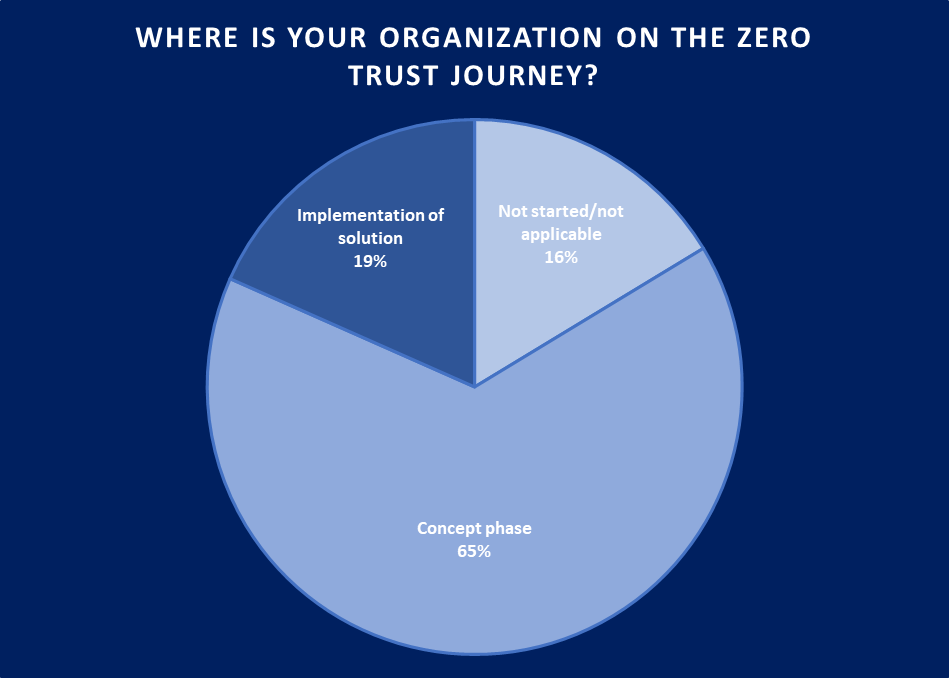
Figure 1: Adoption of Zero Trust is still staggering, due to the complexity of changing IT infrastructures and the gap between concepts and practical implementation (Source: KuppingerCole Analysts)
Only 19% of the respondents to a recent poll conducted by KuppingerCole Analysts are already concretely implementing a Zero Trust approach across their IT and their cybersecurity infrastructure, while two out of three still are in the concept phase. This also explains some growing frustration regarding Zero Trust: While the concept is meaningful, it is a journey to make Zero Trust a reality for a modern cybersecurity infrastructure, helping to strengthen the security posture of organizations.
There are multiple aspects that impact the success of a Zero Trust journey:
- Leadership: A successful Zero Trust journey requires strong leadership, from vision and mission to change management and enforcement of the technical change required. Zero Trust leads to fundamental shifts within IT, with some areas such as IAM (Identity and Access Management) becoming more relevant and others being of lesser importance. Change requires leadership. Most commonly, CISOs are in the lead, backed by the CIO, which is a logical choice due to Zero Trust being primarily about strengthening the cybersecurity posture.
- Organization: Leadership comes with organizational change. Zero Trust impacts many areas of IT, involving the security teams, the IAM team, but also the network teams and, in a broader perspective, also data security and governance as well as software security with the teams behind. Making Zero Trust a reality requires organizational change, at minimum towards close collaboration amongst the various involved parties.
- Architecture: Zero Trust requires major architectural changes. The increasingly established models such as the one from NIST provide guidance. However, applying this to the current state of IT and transforming it into a practical approach and roadmap still remains challenging, also due to the large number of technologies involved.
- Delivery: Last not least, it is about delivery. With Zero Trust impacting so many different areas of IT and being a multi-year journey, there is no fast track to success and there specifically is no silver bullet in the sense of “the one product” for Zero Trust. Zero Trust impacts many areas of IT and cybersecurity and thus requires changes in many areas, multiple of these being closely related.
While leadership and organization always depend on the state of organizations, the most common approach nowadays is having the CISO in lead of the Zero Trust initiative. In most organizations, CISOs are already responsible for not just “core” cybersecurity including network security, but also for IAM as one of the cornerstones of any Zero Trust approach.
With CISOs nowadays commonly being responsible for both cybersecurity and IAM, they are the best choice for Zero Trust leadership.
When taking a broad perspective on Zero Trust, which is strongly recommended, there are other teams that also must become involved. Aside from data security/governance and software security that already have been mentioned, this affects teams that are responsible for FRIP (Fraud Reduction Intelligence Platforms) and frequently also the network teams, due to themes such as SD-WAN, microsegmentation, and others that are affecting both network security and network infrastructure.